| 2013 Target Data Breach | |
|---|---|
| Date | November 2013-December 2013 |
| Location | Internet and USA |
| Methods | Malware |
In late 2013, from mid-November to mid-December, hackers gained access to millions of peoples credit card data and personal information through channels related to {{#NewWindowLink: http://www.target.com/ | Target's }} {{#NewWindowLink: wikipedia:Point_of_sale | point of sale (POS) }} systems. The hackers were able to gain access to nearly 100 million Target customer's personal and financial data. [1]
Overview
As the attack begun, there were several points in which Target could have stopped the attack:
- Target gave network access to a third-party vendor, a small Pennsylvania {{#NewWindowLink: wikipedia:HVAC | HVAC }} company, which did not appear to follow broadly accepted information security practices. The vendor’s weak security allowed the attackers to gain a foothold in Target’s network and allowed consumers data to be at risk.
- Target appears to have failed to respond to multiple automated warnings from the company’s anti-intrusion software that the attackers were installing malware on Target’s system.
- Attackers who infiltrated Target’s network with a {{#NewWindowLink: Passwords | vendor credential }} appear to have successfully moved from less sensitive areas of Target’s network to areas storing consumer data, suggesting that Target failed to properly isolate its most sensitive network assets.
- Target appears to have failed to respond to multiple warnings from the company’s anti-intrusion software regarding the escape routes the attackers planned to use to exfiltrate data from Target’s network. [1]
The hackers not only stole credit card data but also names, phone numbers, addresses, etc. This explain why banks like Citibank announced they were re-issuing all debit cards that were possibly involved in the breach. It’s no longer adequate to just change the Pin numbers as purchasers of the stolen data could simply change the PIN numbers back to whatever they desired with the additional stolen data such as phone numbers and addresses.
Malware Used and Where It Originated
Software Used in Attack: BlackPOS
The software that was used to hack the POS system is a variant on one that is commercially available on cybercrime forums for the robust sum of $1,800 for the “budget version” and $2,300 for the “full version,” which also allows the bad guys to encrypt the data they've stolen. [2] The software is called BlackPOS and in March of 2013, 8 months before the Target data breach, {{#NewWindowLink: http://www.cert-gib.com/ | CERT-GIB }}, the emergency repsonse team of GIB, a security and computer forensics company based in Russia, have seen and interacted with this new type of POS Malware.
The way BlackPOS works is it infects computers running {{#NewWindowLink: wikipedia:Microsoft_Windows | Windows }} that are part of POS systems and have card readers attached to them. These computers are generally found during automated Internet scans and are infected because they have unpatched vulnerabilities in the {{#NewWindowLink: wikipedia:Operating_system | OS }} or use weak remote administration credentials. In some rare cases, the malware is also deployed with help from insiders. Once installed on a POS system, the malware identifies the running process associated with the credit card reader and steals payment card Track 1 and Track 2 data from its memory. This is the information stored on the magnetic strip of payment cards and can later be used to clone them.[3]
Card Shops
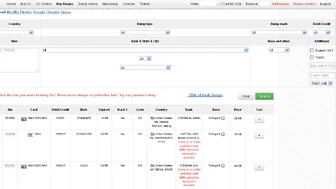
According to the “base” name for all stolen cards sold at this card shop, the proprietor sells only cards stolen in the Target breach. Source: KrebsonSecurity.com
Card shops are websites that list card information including the card type, expiration date, track data (account information stored on a card’s magnetic stripe), country of origin, issuing bank, and successful use rate for card batches over time. The newer the batch, the higher the price, as issuing banks often have not had sufficient time to identify and cancel compromised cards. Those purchasing the information can then create and use counterfeit cards with the track data and {{#NewWindowLink: wikipedia:Personal_identification_number | PIN numbers }} stolen from {{#NewWindowLink: wikipedia:Magnetic_stripe_card | credit and debit card magnetic stripes }}. Fraudsters often use these cards to purchase high-dollar items and fence them for cash, and if PIN numbers are available, a thief can extract a victim’s money directly from an {{#NewWindowLink: wikipedia:Automated_teller_machine | ATM }}.[4]
Privacy and Data Breaches
Following a data breach such as Targets in 2013, millions of pieces of personal data are compromised allowing criminals to purchase their data. Once a criminal purchases their data off one of the card shops in the {{#NewWindowLink: wikipedia:Darknet_(overlay_network) | darknet }}, criminals can use the cards data to purchase goods online or can even code old magnetic strip credit and debit cards with the compromised card data they purchased and purchase goods in stores. This is a quick way criminals can turn their scheme into quick and non-traceable money. Although in this instance credit card data was stolen via a malware data breach, criminals can also acquire data such as this in phishing scams. This is where criminals send out communications to unsuspecting victims asking for personal information to the exploit it.
- ↑ 1.0 1.1 A “Kill Chain” Analysis of the 2013 Target Data Breach. (2014, March 26). Retrieved March 31, 2015, from http://www.commerce.senate.gov/public/?a=Files.Serve&File_id=24d3c229-4f2f-405d-b8db-a3a67f183883
- ↑ Rosenblum, P. (2014, January 14). The Target Data Breach Is Becoming A Nightmare. Retrieved March 31, 2015, from http://www.forbes.com/sites/paularosenblum/2014/01/17/the-target-data-breach-is-becoming-a-nightmare/
- ↑ Constantine, L. (2013, March 28). Researchers find new point-of-sale malware called BlackPOS. Retrieved April 1, 2015, from http://www.pcworld.com/article/2032336/researchers-find-new-pointofsale-malware-called-blackpos.html
- ↑ Cards Stolen in Target Breach Flood Underground Markets. (2013, December 20). Retrieved March 31, 2015, from http://krebsonsecurity.com/2013/12/cards-stolen-in-target-breach-flood-underground-markets/
